Friday, August 21, 2015
CoderXNews
Yes, you heard it right. It's the dirty truth that’s featuring what is being called the largest privacy breach ever.
Billions of cell phone users are at risk of a vulnerability in the SS7 inter-carrier network that allows hackers and spies agencies to track locations and intercept all voice calls from anywhere in the world.
This is something we already know from the last year's Snowden leaks
that explained the National Security Agency (NSA) capabilities to gather nearly 5 Billion records a day on mobile phone locations around the world.
But, it's worse than we have thought.
The famous Australian TV programme "60 Minutes" demonstrated that it is possible for anyone to track cell phone location and intercept calls and text messages.
This time, not due to a security vulnerability in the phone's operating
system, but due to a serious flaw in the very system our cell phones use
to communicate with each other around the world – The global signaling system, called SS7.
Thursday, August 20, 2015
CoderXNews
Web.com Hacked! Credit Card information of 93,000 Customers Compromised
Web.com, a Florida-based web hosting company with up to 3.3 Million
customers, has suffered a data breach and may have compromised personal
information and credit card data belonging to 93,000 of its clients.
The company on Tuesday confirmed that some unknown hackers had breached
one of its computer systems on August 13, 2015, and accessed personal
information of nearly 93,000 customers.
Web.com, with the goal to help small businesses succeed online,
uncovered the unauthorized activity as part of its ongoing security
monitoring and shutdown process.
The stolen information includes:
- Credit Card information
- Actual Names associated with the payment cards
- Residential Addresses
Monday, July 13, 2015
Unknownskype
Skype WebCam Hack
Skype
(play /'ska?p/) is a proprietary voice-over-Internet Protocol service
and software application originally created in 2003 by Swedish
entrepreneur Niklas Zennström and his Danish partner Janus Friis. It has
been owned by Microsoft since 2011.
Many ppl want to view web cam them partner boy/girl friend after skype release 5.1.x version Pakistani Hacker Created exploit which allow to ppl view Webcam without permission Software usage is easy
1 -uninstall all skype which u have already installed
2 - minimum 3 person on convertion call user must be all online in call (many ppl trying to make offline user call to test software not work bcz user need online
3 - skype all use must be on pc online on window or linux Some Os Also support this exploit remove installed dir form to C:Programm file Run Setup of Skype webcam hack and follow the video which exploit creater make there is 2 file 1 is setup if after installing not workng then run Skype-x.exe file which ll patch skype registry
Monday, May 25, 2015
Kazy Bot Full Version ( Cracked)(No Port Forward)
step 1 ) upload files from php folder to your hosting's public_html folder
step 2 ) create datebase with name kazybot
step 3 ) import database file to your kazybot database
step 4 ) connect your server from window client
step 5 ) build server.exe with your server address
==+==+==+==+==+==+>Enjoy Hacking<==+==+==+==+==+==+==+==
Thursday, May 21, 2015
CoderXEbooks, Security, Web Hacking
The Webapplication Hackers HandBook
Chapter 1 Web Application (In)security
Chapter 2 Core Defense Mechanisms
Chapter 3 Web Application Technologies
Chapter 4 Mapping the Application
Chapter 5 Bypassing Client-Side Controls
Chapter 6 Attacking Authentication
Chapter 7 Attacking Session Management
Chapter 8 Attacking Access Controls
Chapter 9 Attacking Data Stores
Chapter 10 Attacking Back-End Components
Chapter 11 Attacking Application Logic
Chapter 12 Attacking Users: Cross-Site Scripting
Chapter 13 Attacking Users: Other Techniques
Chapter 14 Automating Customized Attacks
Chapter 15 Exploiting Information Disclosure
Chapter 16 Attacking Native Compiled Applications
Chapter 17 Attacking Application Architecture
Chapter 18 Attacking the Application Server
Chapter 19 Finding Vulnerabilities in Source Code
Chapter 20 A Web Application Hacker’s Toolkit
Chapter 21 A Web Application Hacker’s Methodology
Chapter 2 Core Defense Mechanisms
Chapter 3 Web Application Technologies
Chapter 4 Mapping the Application
Chapter 5 Bypassing Client-Side Controls
Chapter 6 Attacking Authentication
Chapter 7 Attacking Session Management
Chapter 8 Attacking Access Controls
Chapter 9 Attacking Data Stores
Chapter 10 Attacking Back-End Components
Chapter 11 Attacking Application Logic
Chapter 12 Attacking Users: Cross-Site Scripting
Chapter 13 Attacking Users: Other Techniques
Chapter 14 Automating Customized Attacks
Chapter 15 Exploiting Information Disclosure
Chapter 16 Attacking Native Compiled Applications
Chapter 17 Attacking Application Architecture
Chapter 18 Attacking the Application Server
Chapter 19 Finding Vulnerabilities in Source Code
Chapter 20 A Web Application Hacker’s Toolkit
Chapter 21 A Web Application Hacker’s Methodology
Monday, May 18, 2015
Friday, May 15, 2015
CoderXshell
404 Not Found Private Shell
when we got the admin access we need
to upload shell. After uploading shell we can index deface of a website, server
rooting, cpanel cracking etc. There are many php shell like C99, R57 etc. One
of the best and secure shell is 404 not found private shell. Without password
you can't open it. So if you upload shell in a server without you none can use
it.
So what is it?
After uploading shell when you open
the shell link you can find a page like this:
After move your mouse cursor and fix
it when it get a box for giving a password.
Password for shell -> abc
Wednesday, May 13, 2015
CoderXscanner, SQL injection, tools
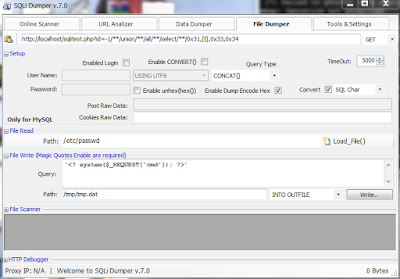
SQLi Dumper - Advanced SQL Injection\Scanner Tool v7.0 Private Version
Designed to be automated to find and exploit web security vulnerabilities in mass from worldwide!
It is robust, works in the background threads and is super faster.
Uses an advanced search engine with 10 different online search services.
Last release: 06/23/2014 v.7.0
It is robust, works in the background threads and is super faster.
Uses an advanced search engine with 10 different online search services.
Last release: 06/23/2014 v.7.0
SQLi Dumper Features:
-Suports 20 methods of SQL Injection;
-Suports Multi. Online search engine (to find the trajects);
-Automated search for data in a bulk URL list;
-Automated analizer and dumper with custom injections points (URL, POST, Cookies, UserLogin or UserPassword);
-Dumper suports dumping data with multi-threading (databases/tables/columns/fetching data);
-Exploiter, Analizer and Dumper suports up to 50x separeted threads;
-Advanced WAF bypass methods;
-Advanced custom query box;
-Dumper can dump large amounts of data, with greats control of delay each request;
-Easy switch vulnerabilities to vulnerabilities (internal database);
-Suports proxies list;
-GeoIP database;
-Advanced Trash System works with millions of urls;
-Admin login finder;
-Standalone .exe (no install).
credit -> http://sqldumper.blogspot.com
Unknownpasslist, Web Hacking, wordlist
Word List Download(sites)
Best sites to Download wordlist...
http://cyberwarzone.com/cyberwarfare/pas...word-lists
http://hashcrack.blogspot.de/p/wordlist-...ds_29.html
http://www.skullsecurity.org/wiki/index.php/Passwords
http://packetstormsecurity.org/Crackers/wordlists/
http://www.isdpodcast.com/resources/62k-...-passwords
http://g0tmi1k.blogspot.com/2011/06/dict...lists.html
http://www.md5this.com/tools /wordlists.html
http://www.md5decrypter.co.uk/ downloads.aspx
Thursday, May 7, 2015
UnknownEbooks, SQL injection, Web Hacking
SQL Injection Bypassing HandBook
Content writers :-
Chapter I:::
- SQL Injection: What is it?
- SQL Injection: An In-depth Explanation
- Why is it possible to pass SQL queries directly to a database that is hidden behind a firewall and any other security mechanism?
- Is my database at risk to SQL Injection?
- What is the impact of SQL Injection?
- Example of a SQLInjection Attack
WebApplication Firewalls::
- Detecting A WAF
- Prompt Message
- Dotdefender
- Observing HTTP Response
Chapter II
Advanced evasion techniques for defeating SQL injection Input validation mechanisms
Web applications are becoming more and more technically complex. Web applications, their
- Whitespace
- Null Bytes
- SQL Comments
- URL Encoding
- Changing Cases
- Encode to Hex Forbidden
- Replacing keywords technique
- WAF Bypassing – using characters
- HTTP Parameter Pollution (HPP)
- CRLF WAF Bypass technique
- Buffer Overflow bypassing
Chapter III
Let's see the matter in an orderly fashion from the beginning
- See If Site vulnerability Or Not
- Get Column Number
- Bypassing union select
- Get Version
- Group & Concat
- Bypass with Information_schema.tables
- Requested Baypassing
Chapter IIII
Other issues related to the subject
- Null Parameter
- FIND VULNERABLE COLUMNS
- Count(*)
- unhex()
- Get database
Monday, May 4, 2015
AndroRAT
Androrat is a client/server application developed in Java Android for
the client side and in Java/Swing for the Server.It has been developed
in a team of 4 for a university project. It has been realised in one
month. The goal of the application is to give the control of the android
system remotely and retrieve informations from it.
Download -
Download -
njRAT
The notorious remote access Trojan (RAT) known as njRAT is making a
comeback, according to security firms Zscaler and PhishMe.The RAT,
developed in .NET, allows attackers to take complete control of an
infected device. The malware is capable of logging keystrokes,
downloading and executing files, providing remote desktop access,
stealing application credentials, and accessing the infected computer’s
webcam and microphone.PhishMe reports that njRAT has been distributed
over the past period with the aid of spam emails advertising a car
changer hack for the “Need for Speed: World” video game. Zscaler also
noted that video game cracks and application key generators are often
used as lure.
Download Here->
Download Here->
Wednesday, April 29, 2015
UnknownWeb Hacking
Best Deface pages Collection
Don't Have Time for designing A Deface page .. ??
dont worry here you can download Best Deface Pages,
Just replace the Name and messgae with your own name and message !!
[Click on Download And Copy The Code, Then Use it, for demo you can paste the code on Pastehtml.com
How to edit and save it... ??
All html codes are shared on pastebin, copy it and paste in notepad
then edit it and save as index.html or anyname.html
1- Tiger M@te's Deface Page,
This Deface page was uploaded on google bangladesh'd domain Google.com.bd
: Download
2- Happy Birhthday Deface Page
for making someone's Birthday special =)
: Download
3- Deface Page For Long Messages + Video
Designed By Ffessxt Prince indishell
: Download
4- #opFreedom Plestine,
Deface page with free palestine message, Designed by The Hackers army
: Download
5- Lovely deface Page for Your Girlfried or loved one
This Deface Page was designed by me =)
: Download
6-Deface Page with dancing firefox script
: Download
7-Multi colour deface page
: Download
8- Simple Black Deface Page
Designed by Hax root
: Download
9-Matrix Style Deface Page
Designed by ShOrTy420
: Download
10-Pro Style Deface Page
: Download
9- Awesome #opFreedom Plestine Page with New Fuctions
this page desgned by Syakila Daniel
: Download
10- Awesme Matrix style Deface Page
Designed by coded32
: Download
11- Romantic deface Page with Roses
designed by Deepak Carpenter
: Download
12- Deface Page with Jquery
Designed by Privatex
: Download
13- #opmegaupload Deface Page
: Download
14- A Progammer's Deface Page with Love Letter
Designed by Me .. =)
: Download
dont worry here you can download Best Deface Pages,
Just replace the Name and messgae with your own name and message !!
[Click on Download And Copy The Code, Then Use it, for demo you can paste the code on Pastehtml.com
How to edit and save it... ??
All html codes are shared on pastebin, copy it and paste in notepad
then edit it and save as index.html or anyname.html
1- Tiger M@te's Deface Page,
This Deface page was uploaded on google bangladesh'd domain Google.com.bd
: Download
2- Happy Birhthday Deface Page
for making someone's Birthday special =)
: Download
3- Deface Page For Long Messages + Video
Designed By Ffessxt Prince indishell
: Download
4- #opFreedom Plestine,
Deface page with free palestine message, Designed by The Hackers army
: Download
5- Lovely deface Page for Your Girlfried or loved one
This Deface Page was designed by me =)
: Download
6-Deface Page with dancing firefox script
: Download
7-Multi colour deface page
: Download
8- Simple Black Deface Page
Designed by Hax root
: Download
9-Matrix Style Deface Page
Designed by ShOrTy420
: Download
10-Pro Style Deface Page
: Download
9- Awesome #opFreedom Plestine Page with New Fuctions
this page desgned by Syakila Daniel
: Download
10- Awesme Matrix style Deface Page
Designed by coded32
: Download
11- Romantic deface Page with Roses
designed by Deepak Carpenter
: Download
12- Deface Page with Jquery
Designed by Privatex
: Download
13- #opmegaupload Deface Page
: Download
14- A Progammer's Deface Page with Love Letter
Designed by Me .. =)
: Download
source: http://www.devilcafe.in
Subscribe to:
Comments (Atom)